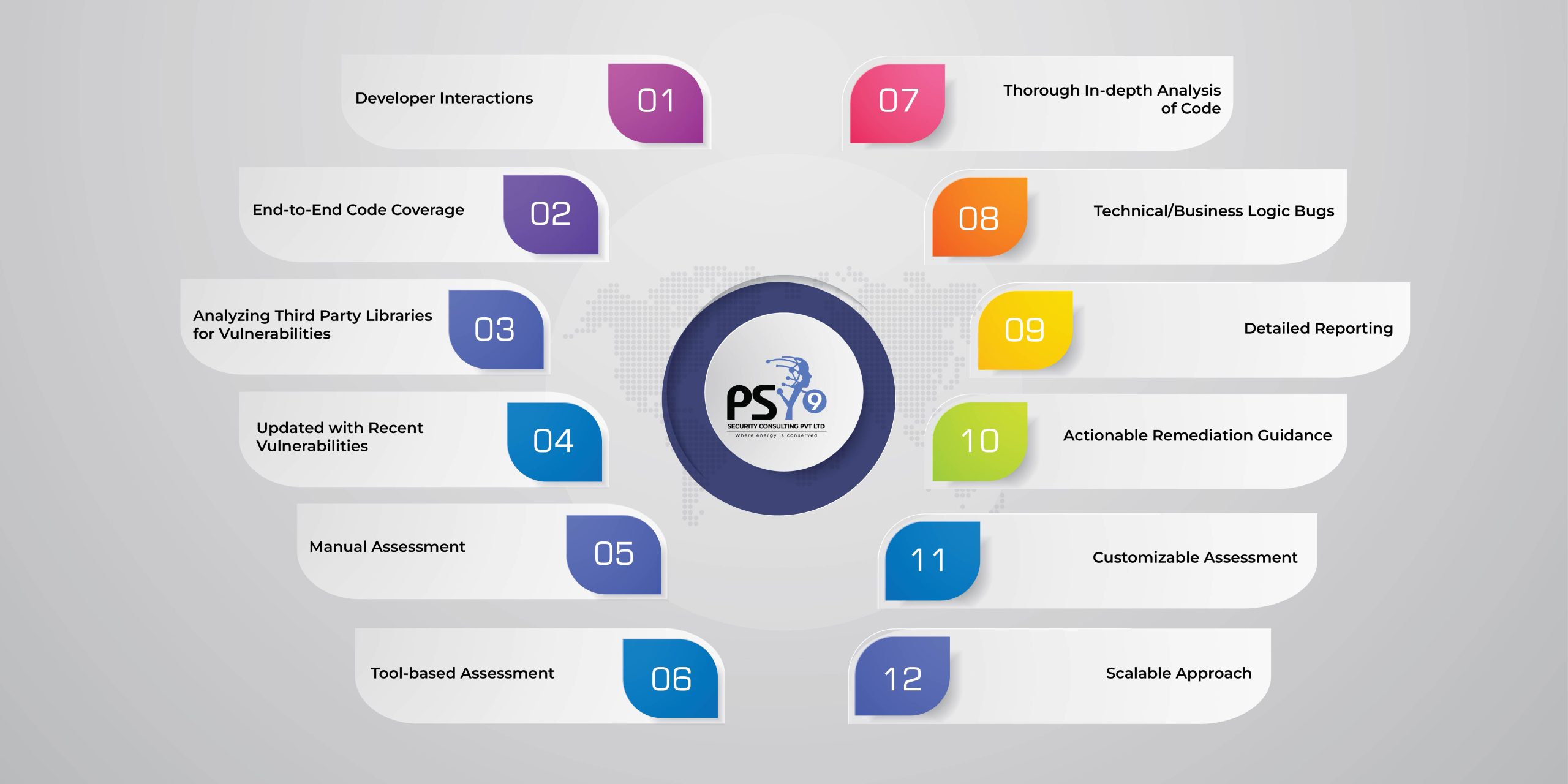
The Source Code Review (SCR) that Psy9 performs is a methodical and secure evaluation of the software system and application code file. it’s for Security Loop Holes, Bugs that were intentionally introduced, designated as safe, and left unchecked during the development of applications and software systems.
There are occasions when certain applications and software systems may have flaws that enable attackers to steal sensitive information, resulting in the loss of tangible assets and secure knowledge. Verifying the implementation of important security controls involves reviewing the code file. Additionally, it examines the code for design faults and unearths any applications’ and software systems’ covert vulnerabilities.
Source code analysis not only shows that the statement on that line of code is ineffective, but it also identifies the incorrect variable that is the vulnerability. This gives application developers a way to curtail the description of each vulnerability case, enabling them to swiftly understand the problem.